Top 5 Deadliest Ransomware: Everything You Need to Know About It
What is malware?
Malicious software also known as malware is an umbrella term used to refer to disruptive or hostile software. It includes computer viruses, Trojans, spyware, adware, scareware, ransomware and other malicious programs. This malware affects your data security where some malware are meant to theft your data or to spy on your data, some other block your access to your data on the system. Different malware like locky ransomware, Petya ransomware, and others affect your data security differently and have become the cause of worry for most of the users today. There is certain anti-ransomware programs and software as well like locky ransomware removal, which offers some relief to these malware attacks.
What is ransomware?
Ransomware attacks have gained the notorious image and been talked widespread in recent times, as the ransomware attack count goes up to 4000 attacks on an average per day. Ransomware locks your system and asks for a ransom to release data. It encrypts your files and proves to be the hard task to get rid of it, as one left with two options, whether to pay for data release or get the data back up on time with Right Backup.
Although ransomware is mushrooming these days we can discuss top 5 most deadly ransomware here, which are causing great trouble for users around the world.
The Top 5 Scariest and deadliest ransomware
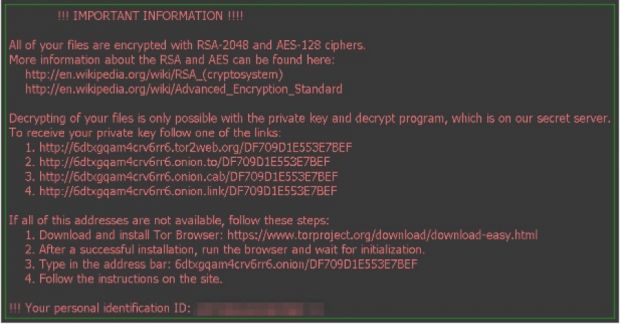
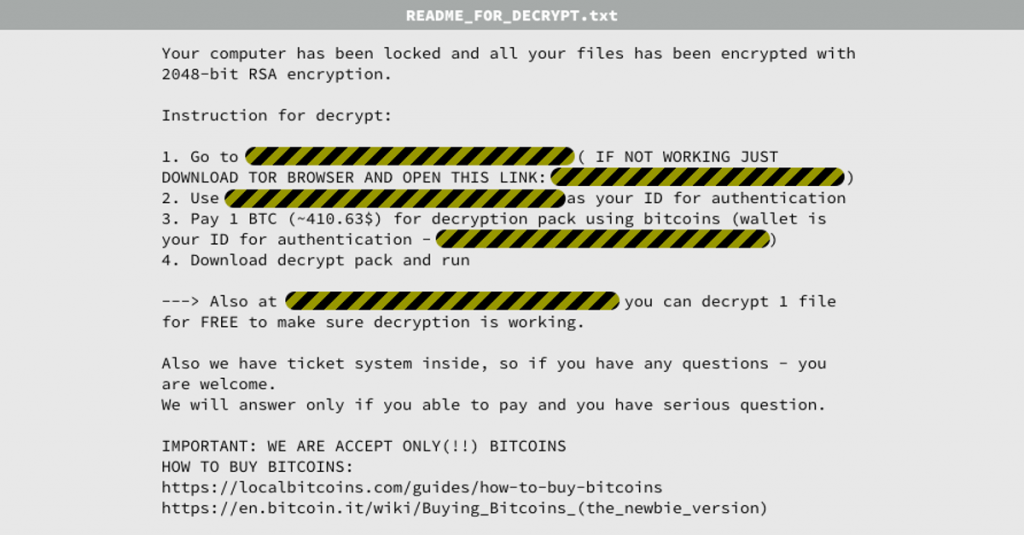
Locky ransomware: This ransomware is meant to lock you out of your data on the system, which is eventually a part of any ransomware but Locky changes your file extension to keep your data away from your reach. It encrypts your files and changes your file extension to lock your data. It uses ‘.locky’ as it’s file extension and it fend the files with RSA-2048+AES-128 encryption.
This is considered to be one of the most dangerous ransomware till now. It generally targets systems with spam email attachments. Once you download the attachment, locky ransomware gets installed on the system further to lock your files and data. Despite all issues related to this ransomware still it is not a good approach to pay to release your data affected by locky ransomware as by applying certain locky ransomware removal steps, you can prevent your data loss to some extent.
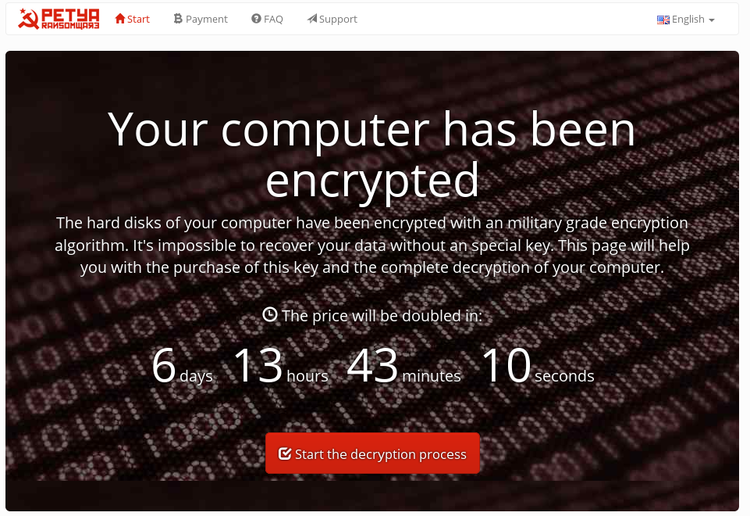
Petya: Petya ransomware attacks differently to the system as instead of encrypting files one by one, it blocks access to the full system by attacking low-level structures on the disk. The Petya ransomware attacks system’s boot drive’s existing master boot record, with an affected and malicious loader.
The affected system’s MBR is overwritten by this malicious boot loader that loads a tiny malicious kernel, which further proceeds with more encryption of data. This way it encrypts a portion of system’s hard drive. This even blocks the access to Windows thus you cannot access the system at all. This ransomware is delivered via spam emails to target systems. Another malicious payload is Mischa, which is considered to be the updated version of Petya ransomware.
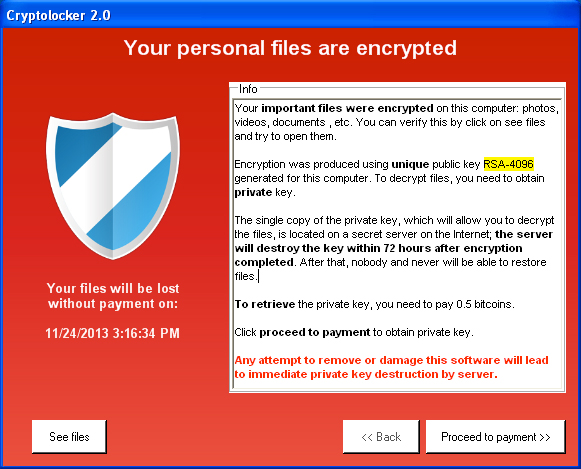
CryptoLocker: It is considered to be one of the nastiest ransomware as it not only prohibits you from your data access but once attacked by this malware you can lose your important data permanently as well. This ransomware is spread through malicious attachments via emails considered to be from some well know institution or company. This ransomware encrypts your data and asks for payment to release it. CryptoLocker virtually locks down your system for further use.
KeRanger: This is the first ever ransomware, which has attacked Mac. Palo Alto Networks has discovered this first Mac ransomware, called KeRanger, which was found infecting the Transmission, a widespread open-source platform for file sharing, which has affected the BitTorrent client. This ransomware is able to encrypt everything in the user’s folder, along with files having common document extensions found in the volumes folder.
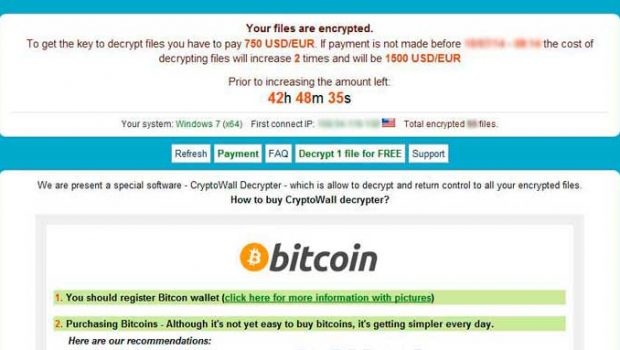
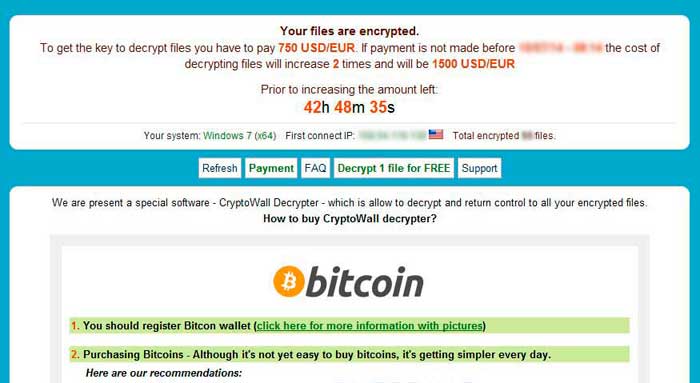
CryptoWall: CryptoWall is from the family of file-encrypting ransomware that first appeared in early 2014. It is primarily distributed using various exploit kits, spam campaigns, and malvertising techniques. This ransomware attack system’s in a fashion similar to CryptoLocker, and it attacks especially important files and data in victim’s system, like tax receipts, bills, financial data etc. Further, it asks for a ransom of few hundred dollars, which can be doubled by a specific period of time.
Recently, CryptoWall has been updated to version 3.0, which has made it more dangerous than ever. CryptoWall encrypts the user files by the system of intelligent scanning and them it generates a unique link for the user. It enables them to hide the identity of the attackers and make government agencies harder to arrest them.
About the author:
Yogesh Sharma is working at http://blogs.systweak.com, as an SEO analyst and technical Content Writer. His forte of writing is ransomware, virus, windows and mac and he is keen interested in writing other technical blogs. You can also find him on Facebook, Twitter and LinkedIn.