LATEST
Casino, Legal drugs & Health
A Guide to Finding the Best Online Casino Sites
There are hundreds of online casino websites out there on the internet, and plenty that are highly rated among players. So, finding the best online casino comes down to striking
Bibhuranjan
- 29 March, 2019
Editor's Pick
How to Get Wax out of a Nectar Collector
A nectar collector is, quite simply, one of the best pieces of vaping equipment that you could ever own. Vaping concentrates
Bibhuranjan
- 24 November, 2023
5 Essential Factors to Consider When Selecting a Closed Pod Vaping Device
The popularity of vaping can’t be downplayed. This trend can be attributed to perceived safety, convenience, flavor fullness, and social movements.
Sunit Nandi
- 3 November, 2023
Vaping Unveiled: How Disposable Vapes Revolutionize Smoking Experience!
How do Disposable Vapes Work Technically? Disposable electronic cigarettes, also known as “disposable vaporizers” o “disposable vapes” have become increasingly popular in
Bibhuranjan
- 2 August, 2023
Ways Property Systems Influence Efficiency and Household Wellbeing
Property systems play a crucial role in maintaining both the comfort and efficiency of any household. From managing temperature and air quality to supporting electrical needs, these systems quietly ensure that homes operate smoothly. When systems are properly maintained, they allow families to focus
- 6 March, 2026
Common Smart Home Mistakes First-Time Users Make
The transition to a smart home can be challenging for individuals who have never lived in one before, despite the fact that it has the potential to make life simpler, safer, and more efficient. In the same way that Tong its Star best licensed,
- 5 March, 2026
Telecom CPQ: Challenges and Best Practices for Quoting Telecommunications Services
Quoting telecommunications services is fundamentally different from pricing standard subscription products. Telecom offers depend on service location, infrastructure availability, vendor sourcing, contract structure, and ongoing lifecycle changes. Unlike traditional industries where pricing is derived from static price books, telecom quoting requires dynamic validation across
- 4 March, 2026
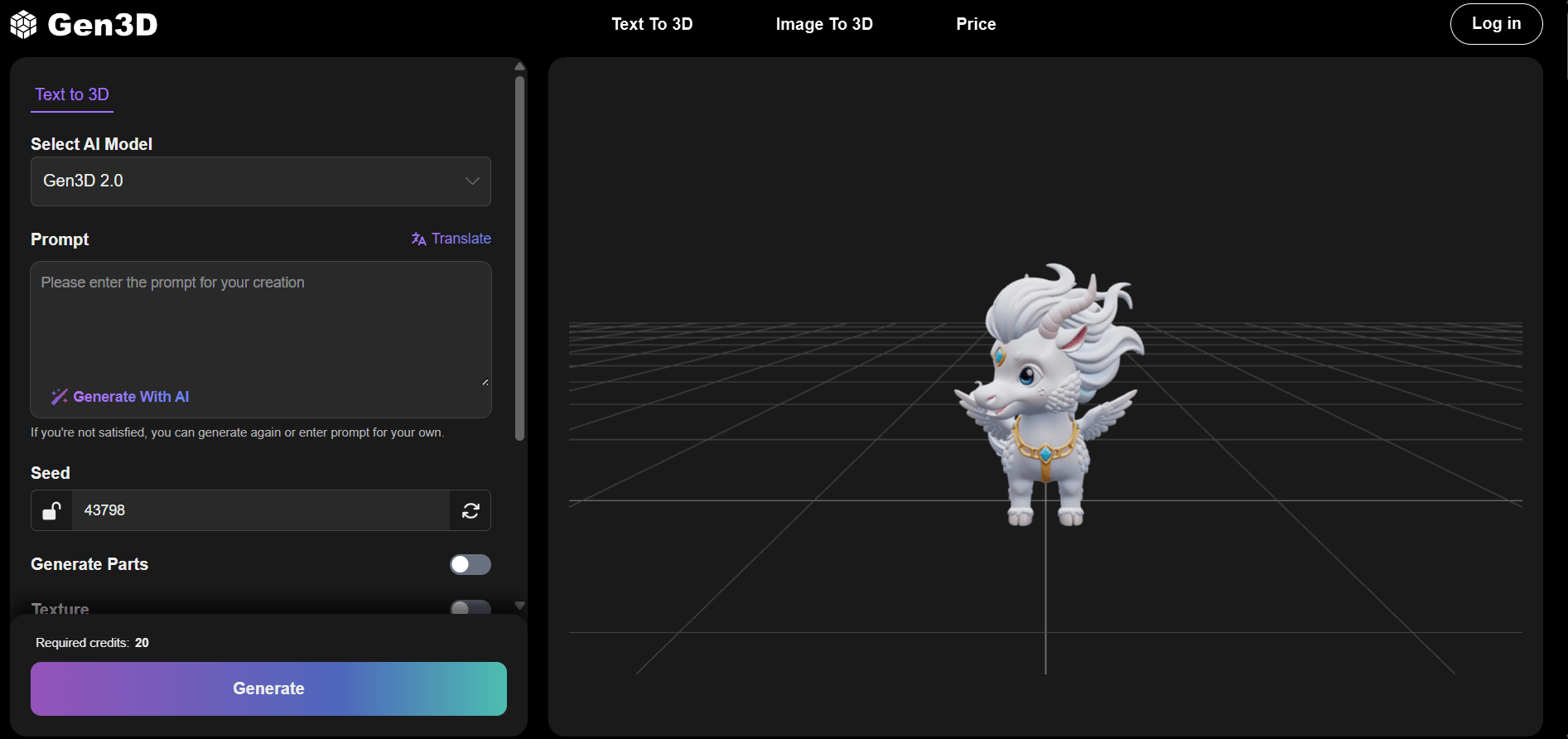
How AI 3D Generator Can Enhance The Visual Competitiveness of Brand Content
In an era of information overload, people take an average of just 3 seconds to determine whether they want to continue engaging with your content. So, is your brand visual enough to make users stop? Traditional graphic design is increasingly becoming homogenous, and the
- 3 March, 2026
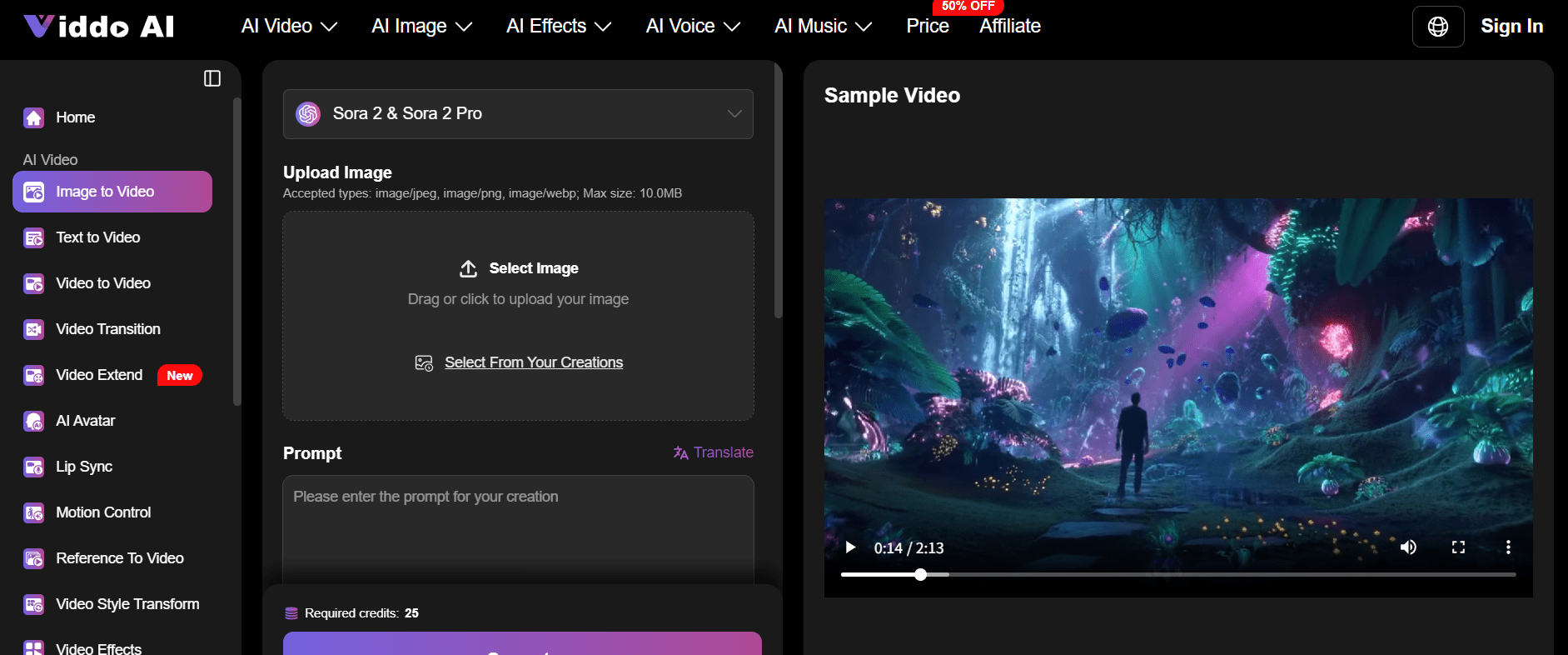
AI-based Efficient Brand Video Production Workflow
Reality shows that they need to produce them much faster than traditional production methods allow. While all of these factors are required by brands to be successful in their respective industries, traditional production models are not capable of producing all three attributes (quantity, speed,
- 3 March, 2026
From Cold and Icy to Warm and Human: How AI Humanizer Tools Are Transforming Content Creation
Content creation isn’t an issue of lacking capability — it’s a challenge of sustaining one’s creativity over time. For example, one’s inspiration is often present within the first 10 minutes of writing, with obvious structure beginning to form; however, eventually the flickering cursor creates
- 3 March, 2026