Levels of security: From incognito to VPN
When it comes to keeping your information safe online, it’s sometimes hard to know which is the best route to take. Whether you’re looking for privacy from marketing companies, your internet service provider (ISP) or the prying eyes of would-be hackers, there are different levels of privacy and security to be found online in the various tools available.
Past installing antivirus and using a lengthy, difficult-to-remember password, knowing what to put in your security armoury can feel confusing and complicated at times. It’s a misconception that something as simple as incognito browsing can serve the same purpose as a proxy or a VPN, and even well-known names like Tor have been found to lack the privacy they were created to offer.
So what’s what, and what is it all good for? Here are a few options for privacy and security that you might use or have considered using, summed up in terms of what they offer and what they don’t.
Least secure: Incognito browsing
Using an incognito browser gives you a similar end result to clearing your browsing history after you’ve been online. It stops your browser, such as Chrome or Firefox, from remembering what you’ve viewed or filled out in online forms, and stops cookies from being saved. In doing so, it prevents other people who log onto your device from being able to see what you’ve done online.
The main problem with incognito browsing is that your activity can still be visible to the websites you’re looking at, as well as your ISP. Your device’s unique IP address isn’t hidden, which means that if you’re browsing at work or school, it could be easy for someone at that organisation to see what you’ve been viewing online.
In terms of cyber criminals, this kind of connection is only as secure as the network you’re using – so if you go incognito on free public Wi-Fi, typically an unsecured, unencrypted connection, your data will still be easy to view and steal if a third party does gain access.
Though many browsers suggest that your privacy is protected when browsing incognito, it is only protected from other people using your device. As far as the wider internet is concerned, this is not an effective privacy or security measure.
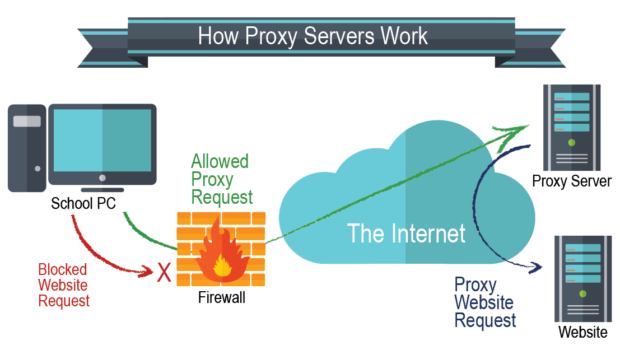
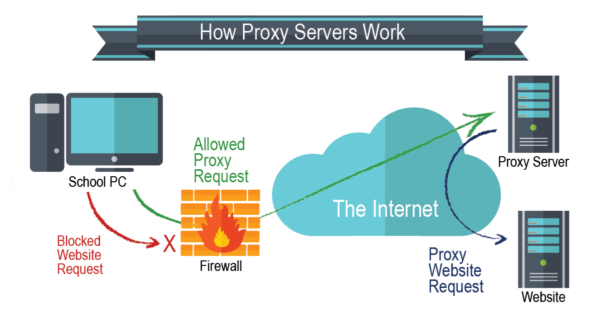
3rd place: Proxy servers
Proxy servers are a definite level up from incognito browsing. The main reason a lot of people choose to use a proxy server is that it keeps your true IP address hidden and shows your web activity as that of an IP used by the proxy provider. Your IP address can help third parties to find out what country you’re based in, what city you live in and what other sites you’ve been browsing – by masking this detail and surfing the internet under the guise of an alternate identifier, your details are that little bit safer.
The issue with proxy servers is that they only secure your browser window itself, rather than your whole internet connection. If you use a proxy to browse a particular website in Chrome or Firefox while running apps in the background, the activity that happens via those apps will not be hidden under an alternate IP and can still be traced to your device.
Another issue is the lack of encryption offered by a proxy. While there are some options for protecting your privacy that secure your data and activities against hackers and other third parties using encryption, a proxy server only hides your IP. Different offerings have different features, but generally speaking they don’t offer end-to-end encryption which would make your data undecipherable to unwanted accessors.
2nd place: Tor
Tor: the infamous worldwide server network developed by the U.S Navy for anonymous internet browsing, and widely adopted by users of the Dark Web who wish to carry out illicit activities in secret online.
The Tor network is run by a non-profit organisation who serve to research and develop online privacy tools, and essentially it disguises your online identity by routing your traffic across a number of different servers. Along the way, your traffic is encrypted so that it can’t be traced back to you. Someone trying to look at activity taking place over the network would only see actions as coming from random parts of Tor, rather than from your own computer or device.
While this may seem like a great offering as far as privacy and security are concerned, there are major issues with Tor. Not least the fact that internet users associated with Tor are more likely than others to find themselves on government watch lists, because of its connections to the Dark Web.
Though it’s very difficult to hack the Tor network itself, getting inside the browser is much easier. Hundreds of Tor users have had their true IP addresses revealed by man-in-the-middle attacks and malware designed for that very purpose. While you might be more likely to get hacked by a government agency looking for criminals on Tor than criminals themselves, it’s worth considering the risk of third party data access.
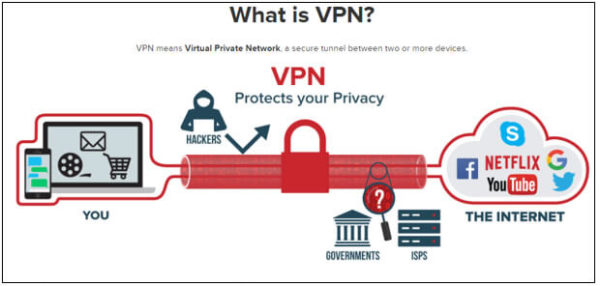
Most secure: Virtual Private Networks
For an encrypted connection that allows you to act under an alternative IP address and which doesn’t have such a high risk of being hacked by a government agency, VPNs are an increasingly popular and efficient choice.
When you connect to the internet using a VPN, your traffic is rerouted through a secure server elsewhere in the world. The whole connection is hidden under a layer of encryption, meaning that if anyone were to try and access your information all they’d see is a collection of nonsensical numbers and letters, rather than things like banking details or personal ID.
Be wary of free VPN services, which have sometimes been found to collect and sell user data, and instead opt for a more privacy-sure paid option.
Any tactic for online security should be backed up with the basics, like antivirus software and regular software updates to keep on top of security patches. Set up two-factor authentication and change passwords regularly, to make sure that however you connect to the internet, you’re set up to keep things as secure as possible.