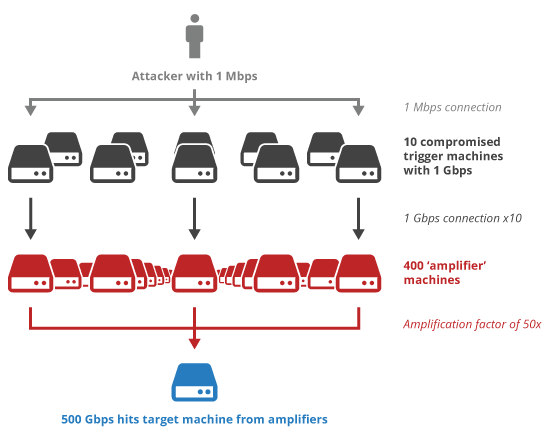
How UDP Enables DDoS Attacks
The Internet is based upon a number of public protocols. These protocols define how computers should talk to one another to accomplish a particular purpose. For example, the Hypertext Transfer Protocol (HTTP) defines how web pages should be carried over the Internet, enabling us to browse our favorite sites. These protocols are carried around the […]