How UDP Enables DDoS Attacks
The Internet is based upon a number of public protocols. These protocols define how computers should talk to one another to accomplish a particular purpose. For example, the Hypertext Transfer Protocol (HTTP) defines how web pages should be carried over the Internet, enabling us to browse our favorite sites.
These protocols are carried around the Internet by protocols such as TCP and UDP. The Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) are designed to meet different needs. TCP is intended to provide highly reliable communications and includes a setup handshake, error correction, and acknowledgement of each packet received.
UDP, on the other hand, is designed to support lightweight communications. While this is an asset for many organizations, the design of the UDP protocol also makes it a useful tool for cybercriminals wishing to perform Distributed Denial of Service (DDoS) attacks.
How Does the User Datagram Protocol Work?
UDP is designed as a very lightweight transmission protocol. Unlike TCP, which uses a handshake to establish a communications channel between two computers, UDP does not require any setup to start communication.
UDP is designed as a request/response protocol. The client sends a query, such as a request for a Domain Name System (DNS) server to provide the IP address associated with the domain google.com, encapsulated within a UDP datagram. Upon receiving this request, the server sends the appropriate response in reply.
This kind of lightweight transmission protocol is essential for systems that require near real-time communications or do not have the processing power or network bandwidth necessary to handle the additional overhead associated with TCP. However, the fact that UDP lacks this connection setup handshake used by TCP also makes it an asset for DDoS attackers.
Advantages of UDP for DDoS Attacks
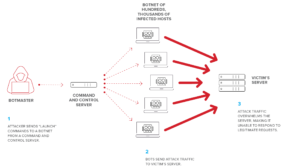
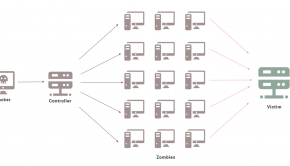
A DDoS attack is designed to overwhelm a target with more traffic or data than it is capable of managing at a given time. All technology has a maximum limit on the number of requests that it can handle or the total amount of data that it can receive, process, or store. DDoS attacks deliberately exceed these thresholds to degrade service availability and usability.
In theory, a DDoS attacker should have to send the same volume of traffic and data as is received by the recipient. However, the properties of UDP and the services that commonly use it enable DDoS attackers to amplify the impact of their attacks.
IP Spoofing
Every packet sent over the Internet has a source and destination IP address. The destination address enables the routers along the way to ensure that the packet reaches its intended recipient. The source address tells the recipient the source of the packet. The source address also enables the recipient to send a response by sending a packet to that address. The source IP address in a packet header is under the control of the sender, meaning that it can be easily spoofed to another address. However, this makes it impossible for the recipient to send a response to the correct machine.
With TCP, a spoofed source address makes a connection impossible since misdirected packets mean that the TCP handshake will not be completed. UDP, on the other hand, has no connection setup phase. The only impact of a spoofed IP address on a UDP connection is that the server’s response will go to the wrong place.
For a DDoS attacker, this is more of a benefit than a drawback. Not only can it make it more difficult to attribute an attack, the use of IP spoofing is essential for DDoS amplification.
DDoS Amplifiers
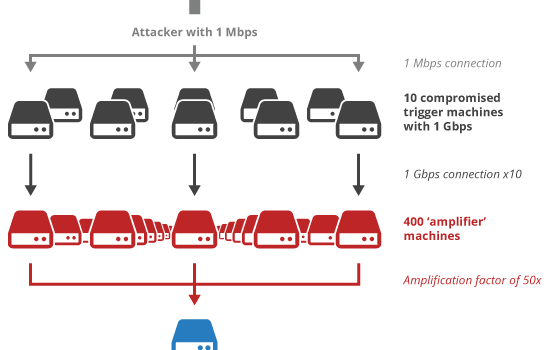
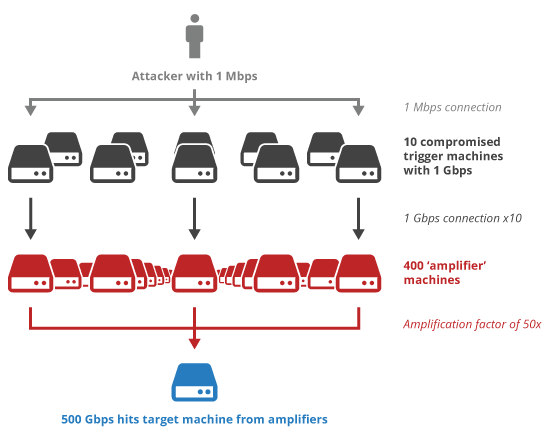
UDP is designed to allow a user to make a request and have a server send a response. In many cases, this response will be larger than the original request, often many times so.
DDoS attackers take advantage of these services that create responses many times larger than the corresponding request. They will send a request to the server with a source IP address spoofed to that of the target computer. After processing the request, the server will send the appropriate response. This results in the target computer receiving a large, unsolicited UDP response.
DDoS amplification enables an attacker’s botnet to send a relatively small amount of traffic but ensures that the target receives a lot. For example, exploiting the NXNSAttack vulnerability enables DDoS amplification factors of over 1600x.
Protecting Against UDP-based DDoS Attacks
The use of DDoS amplification is only one way in which UDP can be exploited for use in DDoS attacks. An attacker can also perform UDP floods or scans designed to force the target computer to waste resources sending ICMP Port Unreachable messages for every closed port.
Protecting against DDoS attacks that take advantage of the UDP protocol requires a DDoS mitigation solution capable of identifying and filtering out attack traffic. DDoS amplification is often identifiable since it includes a great deal of unsolicited traffic from common DDoS amplifier ports (like DNS). DNS floods are marked by massive numbers of simultaneous DNS requests sent to closed ports. A robust DDoS mitigation solution should be capable of identifying these anomalous traffic patterns and blocking malicious requests, enabling the organization to maintain the availability of its services for legitimate users.