Am I Being DDoSed? How Do I Protect Myself?
The past five years has witnessed a surge in DDoS attacks thus causing the DDoS landscape to keep evolving and expanding as time goes by. For many who have chosen not to stay under the protection of a DDOS Protected Server Hosting provider, chances are that sooner, rather than later, there may be an attack which may cripple your online infrastructure.
To better understand DDoS attacks and the severity of an attack on your infrastructure, below are some of the important things you should know.
What Is A DDoS Attack?
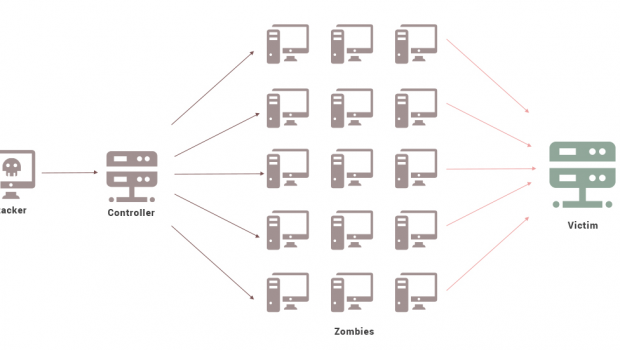
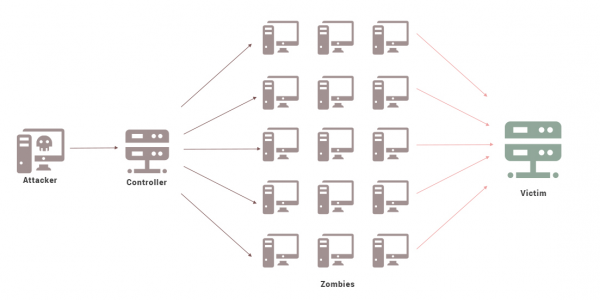
A DDoS attack is also known as Distributed Denial of Service attack. This attack is one of the most nefarious cyber-attacks designed to intentionally disrupt the normal flow of traffic to a server. The attack is also capable of blocking access or normal service users by flooding or overwhelming the intended target with a flood of packets.
The DDoS attacks are principally based on the use of botnets which are leveraged upon to carry out the malicious intents. A botnet which can be a portmanteau of robots and networks, is network of compromised computer system infected with malware which has been designed to alter the normal functions and also to bring down the systems.
Botnets are specifically designed by hackers to flood the target computer and servers with IP packets that cause disruption of access to networks and other assets including application and access by normal users. The DDoS attacks are known to be very notorious and capable of costing businesses unimaginable loss as the shutdown continues.
Who Stands The Risk Of A DDoS Attack?
DDoS attaches are aimed at businesses from all sizes, whether a small business or an enterprise. While an average PC user does not have to worry about such attacks as this, businesses should be wary as they stand to lose several hundreds of dollars in revenue and suffer possible plummeting of shares should the downtime continue for an extended period of time. To mitigate against risks of DDoS attacks, businesses, irrespective of their size must invest heavily in DDOS Protected Server Hosting provider and other security measures designed to counter such attacks.
How Do You Know You Have Been Attacked?
While like several other attacks, DDoS hits the target business without forewarning, there are certain symptoms that’ll give affected persons an idea of the attack. Below are some of the tell-tale signs that your system has been compromised by a DDoS attack.
Service Unavailable Error
When a server is down, one of the very first tell-tale sign of this is the “Service Unavailable” error message which user is greeted with when they try to browse it in a web browser. This error message may however become persistent over a longer period of time and this indicates that the server has become unreachable. For further diagnosis, it is recommended that you make use of the net stat command in Windows, Linux/ Unix systems.
The Net stat is a network command tool that displays the active TCP and UDP ports which a server is listening on. It also provides information on the IP routing table, Ethernet Statistics, and both the IPv4 and IPv6 statistic. Once the information has been displayed, look for unusual activities which may be in the form of a huge rise in number of IP addresses connected to the same port.
Zero Network Traffic
Another common way by which you can diagnose the DDoS attacks is due to loss of network traffic or packet loss to your website or server.
In this case, if you attempt pinging any website or its address, you may discover that it is either timing out entirely or results in a loss of packets.
Checking Nginx/Apache/Webserver Logs
Another way to identify that you are under DDoS attacks is to examine the web server log files. You may want to also check the clients connected to the server by running the command provided below
netstat -ntu | awk ‘{print $5}’ | cut -d: -f1 | sort | uniq -c | sort -n
after running the command, if you notice an unusually high number of connections which exceeds what you’ve been experiencing, chances are high that you may have fallen victim to a DDoS attack.
For Apache, you can access the access logs to view the client IPs sending requests to your server using the command provided below
tail -n 500 /var/log/apache2/access.log | cut -d’ ‘ -f1 | sort | uniq -c | sort -gr
The same command can also be used to gain access to the Nginx access log files.
Protecting Against DDoS Attacks
There are several suggestion as to how to protect against DDoS attacks. Some of the most recommended solutions include:
- Tweaking Nginx parameters
- Modifying worker process connections
- Limiting rate of requests
- Limiting connection rate
- Adjusting timeout parameters
- Limiting size of HTTP requests
- Limiting connections to backend servers
- Blacklisting IP addresses
- Use CSF Firewall in cPanel
- Restrict number of concurrent connections
- Using DDOS Protected Server Hosting provider