Protect Your Business With a Complete DLP System
To protect the organization and keep their clients’ data safe, some companies go to great lengths to educate their employees on the regulations and privacy laws that govern their industry. Their employees are also expected to know and follow the security practices and privacy policies that are in place at work. It’s almost a rite of passage for new hires to endure “Orientation Week,” where they are inundated with information about the company and given a lengthy handbook on the procedures and practices, which they must learn and internalize before they begin work. Other companies lean heavily on the latest technology to provide security safeguards and trust these tools will catch any potential data breaches and deal with them appropriately. While both approaches are appropriate, the best strategy to protect your business from data loss is a combination of technology and education.
Threats to Your Data
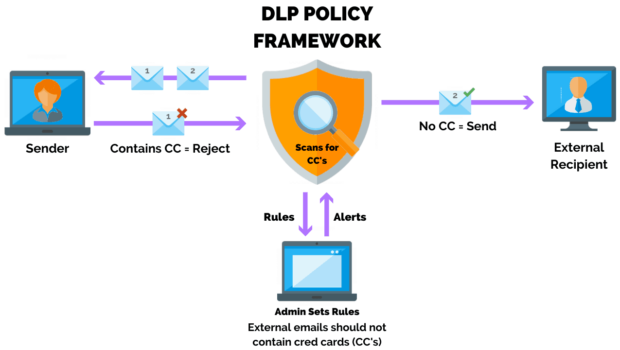
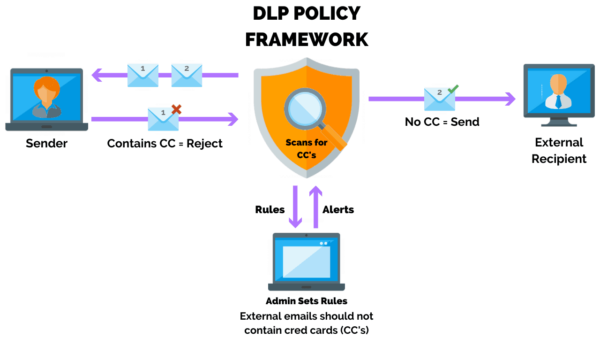
Data loss presents a significant problem for businesses of any size and it can happen at any time — accidentally or deliberately. Unintentional data loss can occur due to power outages, hard drive crashes, natural disasters, liquid damage (like spilling your coffee on your laptop,) and various kinds of human error. Other threats to your data are intentional, including hacking, computer theft, viruses or malware, phishing, social engineering, and more. Unfortunately, data thieves are constantly working to find new ways to steal sensitive information. Data loss prevention (DLP) is a system of tools and processes designed to prevent data from being accessed by unauthorized viewers, misused, or lost altogether. Naturally, DLP is important because it protects your data and reputation, but it also defends your business against interruptions and downtime, degradation of performance, and disruption to customer service.
Technological Solutions
On the tech side of data loss prevention are network security tools that combine procedures, policies, and devices to prevent and respond to unauthorized access to your network. Their function is to prevent data loss in three basic ways: Protection, preventing network security intrusion; Detection, analyzing network traffic and identifying threats; and Response, reacting to intrusions and resolving the threat quickly. There are dozens of cybersecurity tools available that fall into a wide range of categories. They provide what is sometimes referred to as “Defense in Depth,” that is, layers of security that aim to protect your data and network on all levels. Here are a few example of DLP tools:
- Network Access Control allows you to control who has access to your network and allows you to block certain devices or behaviors. It uses analytics so that once you define what behaviors are normal or abnormal, it will alert you when it detects suspicious behavior. You can also install firewalls that block your network from outside sources you don’t trust.
- Email Security applications address the number one threat to your network security. Once hackers gain access to your email and personal information, they can use your email to wreak havoc. Sending spam, viruses, inappropriate content, or blackmail to your clients are just a few malicious things hackers can do with your stolen data.
- Antivirus Software protects against viruses and malware and is one of the most common security tools in use in both personal and business contexts.
- Endpoint Security prevents security breaches, data loss, and viruses in your business network when it’s accessed remotely or through personal devices. This is especially important as it’s becoming more common for employees to use their personal laptops at work or when working from home.
- Wireless Security provides an additional layer of security to your wireless networks, which are intrinsically less secure than wired ones.
Your IT infrastructure and data are at the heart of your business. Because any attack could potentially cripple your entire operation, DLP tools are essential for your company’s health and longevity. A network security expert can evaluate your current solutions, assess their performance, and recommend additional upgrades or safeguards to further protect your data.
Education Protections
One of the most important ways businesses can protect themselves and their data is by properly training their employees. Training should begin right at onboarding with emphasis placed on the importance of cybersecurity and the gravity of data loss and breaches. Procedures should be outlined in the employee handbook and explained thoroughly by trainers. Employees should understand what is expected of them and the consequences of carelessness or breaking the rules. Data loss, theft, and misuse are a constant threat with new hacks being developed every day, so employees must be updated regularly on the latest cyber threats and instructed on how to avoid them using the proper tools and procedures. They also should be certain of what information they are not allowed to share and the circumstances under which they may be asked or tempted to share it. All the technology in the world can’t prevent a data leak over the phone or in person.
Areas that should be covered in employee training are 1) password protection, 2) recognizing phishing and social engineering schemes, and 3) internet and social media policies. Best practices for creating and storing passwords should be taught and strictly followed, which is often a challenge. A solution for this problem is to use a password managing tool that generates strong passwords, remembers them, and allows you to share them within and across your teams. Phishing and social engineering tactics are a little trickier to address. Since social engineering preys upon the desire to help people, employees should be taught how to think critically and recognize bogus requests from potential attackers. Phishing attempts in email can be identified using these protocols:
- Scan any file attachments with an online open-source virus scanner.
- Hover over shared links to see the full address the link will take you to before clicking on it.
- Check the sender’s name against the email address it came from.
- Look at the format of the email to see if it’s suspicious.
- Make a phone call to the sender if you’re unsure.
Policies concerning internet and social media use should be clearly outlined and adhered to by all employees. Understanding general internet safety rules and how to avoid cyber-attacks, phishing, and social engineering schemes on social media platforms is a must. Not only is it important from a security standpoint, but it also can cross privacy boundaries, posing legal risks and threats to your company’s reputation.
Because different industries require different measures of protection, employees need to be briefed on all the necessary tools, procedures, and rules that apply to your particular business. For instance, HIPAA laws for the medical and health industries, GLBA laws for the banking and finance industries, and the California Privacy Act are a few examples of specific regulations that govern privacy and data protection. While those used to be separate entities, privacy and cybersecurity are now converging, making a robust DLP system all the more necessary.
Defense in Breadth
Combining thorough cybersecurity education with a broad range of the latest, most effective tech tools provides your business with more than just “defense in depth,” but “defense in breadth,” as well. To do this, you need buy-in at all levels, from your C-Suite to your administrative assistants. Building habits, holding regular training sessions, setting reminders — even holding cyber-attack drills — will support your network security tools for a complete DLP system. Your business is worth every effort to have the best possible system in place.