5 Simple Data Protection Tips
In this time of great disruption due to Covid-19 pandemic, cyber security threat is ever more real. As the contagion pushes the workforce to work from home, cyber scammers and hackers are taking advantage of ill-equipped domestic IT systems.
Usually, domestic internet connections and computers are equipped with basic security features but these are only sufficient for personal use or occasional homeworking. The IT systems are problematic as they do not have IT security architecture capable of handling prolonged periods of remote working and the potential of cyber attacks. A cybersecurity service provider Singapore can help protect an organization’s data through a variety of measures such as regular threat assessments, vulnerability scans and penetration testing.
Over the last week, the US Secret Service has noted an increase in fraudulent emails related to the disease that contain malwares – and targeted towards businesses and their employees. It should also be stressed that working remotely does not exclude employees from the security and privacy regulations, such as the stringent EU GDPR.
Considering the increased incidence of cyber attacks and the need to comply with stringent privacy regulations, IT security experts remind businesses to work closely with a trusted cybersecurity service provider singapore and to take extra precautionary measures to mitigate any potential risks.
Here are some simple data protection tips for both businesses and individuals in this time of Covid-19.
Keep systems and software updated
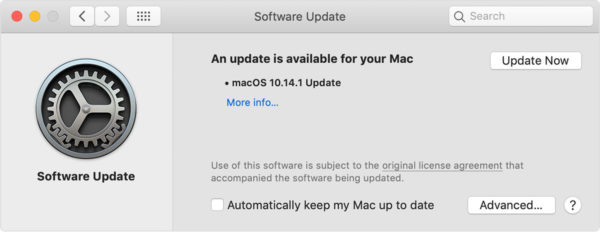
Be sure to use the latest operating system and keep abreast with software updates as they are released. If employees will be assigned to work remotely, the system should likewise use the most recent computer programs. Caution should be taken whenever using domestic IT assets with antiquated software are easy targets for cyber criminals.
Use data-appropriate encryption
Back in the days, data encryption was necessary only for sensitive data. But today, it is a must for any data, whether it is stored on physical server, in-transit data, or transmitted through cloud services.
Choose an encryption solution with algorithm that is appropriate to the data. For basic user information, look for Advanced Encryption Standard (AES) of at least 128-bit encryption and 256-bit encryption for highly classified data. Use of HTTPS web connections provides an added layer of protection.
Practice password hygiene

The password is the key to your virtual office. Password hygiene is vital to safeguard classified information. Businesses enforce effective password policies. Use codes that incorporate alpha-numeric characters and never re-use old passwords. As much as possible, passwords should be changed every 90 days.
Password security breach, even with just one employee account, can compromise the entire IT infrastructure. As such, it is crucial for all staff to adhere to company password policies. Regular password audits can help you keep track of employee compliance. Password hygiene should be strictly enforced especially when remote work arrangements will be implemented.
Ensure crisis resilience

Data backup and recovery should be implemented alongside active data protection strategies. , IT security specialists at Firewall Technical recommend that aside from preventing an actual data breach incident, a risk management plan should be put in place in case hackers successfully infiltrate your security protocols.
Implementing strong data backup and recovery procedure can prevent data loss from accidental damage. Digital data can be stored on a secure cloud server that can be easily tapped to recover data once the system is back.
Avoid external connections
Another simple data protection strategy is to avoid the use of external devices on computers that handle business processes or store classified data. USBs are risky as they can introduce unwanted malware into a computer – and once it has accessed a part of the system, it can compromise the entire IT infrastructure.
If possible, deactivate any external port of devices attached to the IT system. There should also be strict policies with regards to use of external devices in the workplace. If there are plans to work-from home, employees should be encouraged to access data through cloud servers instead of transferring them using an external device.