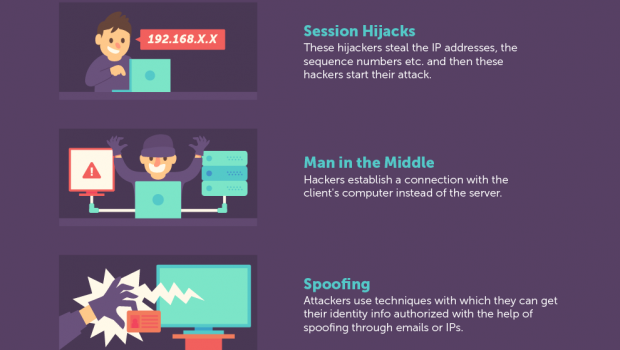
The Dangers Of Free VPN [Infographic]
Using virtual private networks is one of the best ways to keep your data safe from unauthorized access. Nonetheless, there are instances when using them could spell more danger than accessing the internet directly. The infographic below is a good place to check what could go wrong if you decide to use fraudulent or incompetent VPN services.
Accessing the web via VPN guarantees anonymity and other privacy features that will help you navigate the web unexposed. The majority of these VPN providers have pumped up the demand for their services by offering free privacy services, while other established names in the cybersecurity space are paid options.
Naturally, free services are a more attractive offer. However, they always come with a certain level of risk.
You should know that maintaining VPN servers does not come cheap. So why would anyone run a business which doesn’t guarantee a solid return? In most cases, these service providers make up for these losses by flooding their apps with ads. Some even go as far as selling the information of their users to third parties.
Both scenarios defy the purpose of VPNs, as we use them to either escape the unauthorized transfer of our private details or avoid the risks that come with malicious ads. Deploying ads on VPN apps is not the problem itself. It is the source of the ads and the success of the server’s data security systems that are the major areas of concern.
In addition, free VPN services do not offer premium plans which guarantee that there are no loopholes for attacks. Free VPN usually includes outdated data encryption protocols, limited bandwidth, and tracking or data logging.
Understand that utilizing a VPN is like exposing your sensitive data to attackers. Therefore, it is imperative that you understand how VPNs work. What is the particular VPN service you plan to use? How does it work? How well will you be protected?
For more information, check out the infographic below.