5 Tips to Internet Monitoring
The internet of things (IOT) is among the current transformative innovations in the technology world. It allows companies and individuals to connect various devices to achieve different functions. Despite the effectiveness of IOT, it is also a threat because of your data. The company’s or an individual’s information shared on the devices is accessible by unscrupulous data miners such as hackers. Therefore, it is essential to introduce tools such as Blockchain technologies for internet monitoring. Internet monitoring helps you to control the information to balance accessibility and promote privacy. Here are a few tips to internet monitoring:
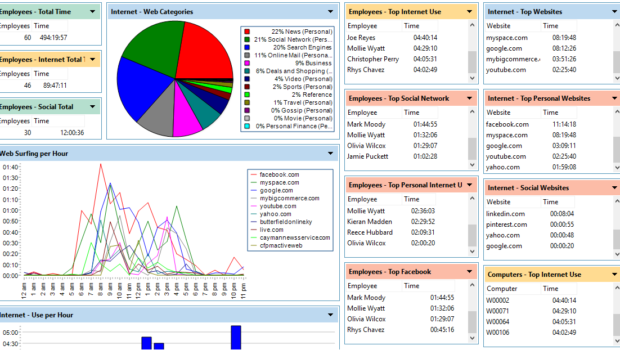
1) Visualization
Path ensures that you monitor the traffic on your website, app, or network productively in a bid to make rational moves to optimize the operations of these platforms. This feature will help you gauge how the traffic affects your services from different parts of the world. A company can make adjustments that will enhance visualization to avoid any defaults.
2) Provide Tokenized Information
Some companies have a token provision that allows users to pay directly using tokens or purchase them. Tokenized information is suitable for business websites that do not prefer intermediaries during payments such as a bank. Use of tokens has been productive over the years, and most individuals participate in the live sales hosted by IT websites. Tokenized information also helps to achieve a balance between privacy and accessibility. Personal or business information is not displayed when using tokens. They act as a substitute for the data, so confidentiality is maintained.
3) Avoid Centralized Networks
You can share information miles apart using devices connected to the internet via a centralized server. However, centralized servers are prone to hacking at it is easy to access all the essential information. Blockchain enhances internet monitoring through the use of a decentralized ledger system. It ensures that a series of data is shared among a network of computers and maintains parity through the use of consensus algorithms. Installing a decentralized network means that your information is not managed by a central authority, so it minimizes the risks of hacking.
4) Use Tools That Are Difficult To Interfere With And An Alerting System
Blockchain technology is an excellent example of an internet-monitoring tool that is hard to alter. Some hackers with breach privacy and businesses have no idea of what is happening. Using such tools makes it difficult for a breach to occur by ensuring the data is intact and secure. It is essential to have an alert system that notifies you in case of any interference with your services.
5) Constant Updates And Reviews Of The Monitoring Tools
As technology advances so are the threats. It is crucial for a company or individual to review the functionality of monitoring tools to ensure that the performance is at a 100%. In case of any improvements in the technology of the devices used, ensure that you update your system of networks. Alternatively, you can also adopt a new strategy or software that is compatible with monitoring needs. This approach is useful for performance and uptime monitoring. Interactions testing should also be done to ensure that the vital functions are operating well.