Understanding privacy VPN in nutshell
What is a VPN and VPN servers? Before we try to address the question, let us first dive into the world of mobile applications and Internet. Today just about anybody is carrying a portable device with multiple applications on it transmitting real-time data that is being shared with corporations, companies, ISPs and governments. There is just tremendous possibility of dating mining and analysis from it.
Well, humans have always been into privacy about what they own and other things like their future plans etc. Technology we have in our pocket that we have no control over is steadily exposing everything that we didn’t want in real world to artificial intelligence. Beware! it is more scary than it sounds if you study it further. But, this post isn’t about developing a sense of fear, instead, we are here to make you aware of the bare minimum protection you can avail to secure your data in transit and more.
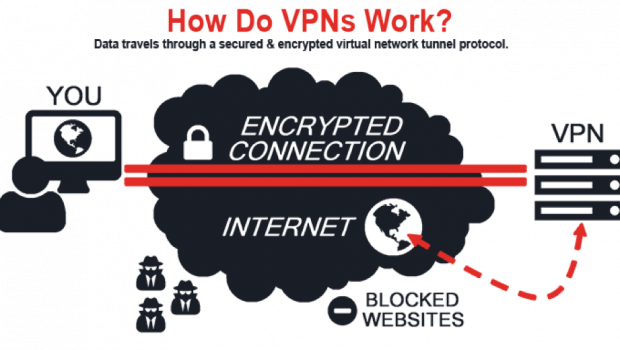
VPN stands for Virtual Private network, it was originally designed to connect business users or professionals back to workplace or home offices using a secure, encrypted, obfuscated protocol. Bare minimum setup includes a VPN server that you connect to from a VPN client, which is on your PC or mobile devices. But owing to the nature of generic VPN setups, what it also does is changes your Internet external IP, hence it also happens to be a privacy or proxy service. In plain text, you get the external IP of the VPN server that you connect to. All the internet activities you do when connected are traced back to the VPN server you connected to. That is one function of the privacy VPN provider. It also helps you with security for example when connecting to your secure business email server over public wifi network. It is advised to use a VPN to prevent any one in between your mail server and your web browser or email client from snooping. So, it helps you gain additional security than what TLS or HTTP(s) offers and prevent malicious data analysis. There are more functions to a VPN than its original ones. Like a VPN server can give access to a dedicated Public IP with open ports for a guy at home in a third world country or a group can use it for gaming or file and/or resource sharing when connected.
Having known this, we must look into the concept of privacy by policy that any privacy VPN offers. It is their word that we take as a promise that we believe they won’t break. A VPN connection isn’t really anonymous as the VPN server admin can actually see pretty much anything you do when connected to a VPN server. Hence, a service provider like NordVPN or Tunnelbear that legally makes it possible for you to connect to VPN gateways or external IPs from various locations without keeping any user-identifiable logs on users.
Before we start with any thing at all, lets first have a word about privacy. Privacy and being able to be anonymous online all depends on your awareness of the issues involved. By getting a new dynamic IP address from a quality privacy VPN provider, you are moving a step ahead in the race but its an ongoing process. It would require you to get acquainted not only with the technicalities but also with general operational security stuff. Basically, you must know that you cannot erase stuff or go back in time and undo things when you are online just like in real life. As a rule presume that everything you do online is either being logged or is monitored.
Getting a privacy VPN isn’t enough until you are aware of the general leaks involved, which are as follows:
DNS | IPv6 | WebRTC | VPN firewall
DNS
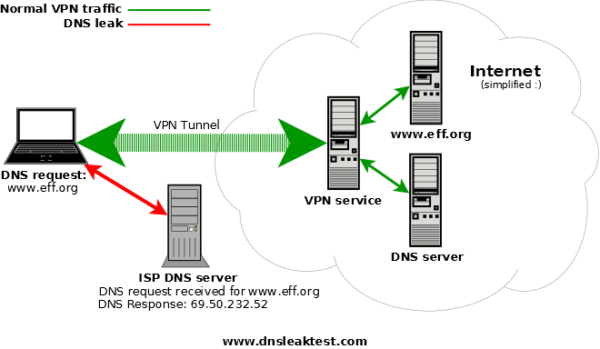
DNS or Domain Name System translates more readily memorized domain names like (www.whatismyipaddress.com) to the numerical IP addresses needed for the purpose of locating and identifying computer services and devices with the underlying network protocols. When you type a domain name in a web browser’s address bar, what happens is your browser first asks your DNS server if its available at an IP to connect to.
DNS leaks can be defined as a situation where you are using your ISP’s DNS server or some other DNS server while you are connected to a VPN service or server. There are a lot of things that could go wrong and it depends on what you want to do with a VPN. The generic DNS leak that happens is your ISP ‘s DNS server or any other DNS server’s ability to log queries like this IP (VPN IP) asked for www.whatismyipaddress.com at this time and they could be recording a number of other identifiers depending on their policy.
How to detect a DNS leak?
1. Try a website based DNS leak detection viz. www.doileak.com or www.dnsleaktest.com
(Doileak.com tests for all the most common leaks, including tests for torrent leaks.)
2. Use “dig” command or utility which is available for all major OS(s), by typing “dig nordvpn.com” in terminal/command line and getting the DNS server along with the port used and other details.
In order to prevent DNS leaks, a Privacy VPN must host its own nameservers or DNS servers with are subject to the same privacy policy that is no identifiable information is logged at all.
As a good privacy VPN service provider must push IPv4 and IPv6 nameservers server-side to the VPN client by default. It works flawlessly with all the major GUI clients and command line VPN clients including but not limited to Gnome Network Manager Plugin in GNU/Linux, Windows OpenVPN GUI client, Tunnelblick on OSX etc.
OpenVPN Inc, the developer of one of the most used opensource VPN protocol OpenVPN has developed built-in DNS leaks protection on Windows platform since OpenVPN version 2.3.9. It is a commendable act. One of the factors on which you can judge a privacy VPN provider is whether or not they were one of the earliest adopters of “–block-outside-dns ” which prevents DNS leaks in Windows OS if they offer OpenVPN has their default protocol.
You as a client can also attempt to prevent this DNS leak situation by setting our DNS servers or nameservers as your default DNS servers in your OS respectively in case you are using a non-standard client for VPN which won’t pull the DNS servers pushed by VPN servers.
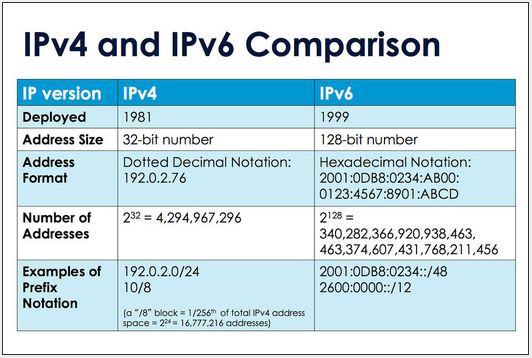
IPv6
IPv6 leaks is nothing but a situation where you could be having an IPv6 connection from your local ISP but your VPN provider is not covering IPv6 and a lot of your IPv6 traffic goes outside your VPN tunnel, causing leaks and issues, ultimately forcing you to either disable IPv6 or change your VPN provider.
A good privacy VPN provider has to offer IPv6 since the very beginning with a vision and understanding that IPv6 is the future.
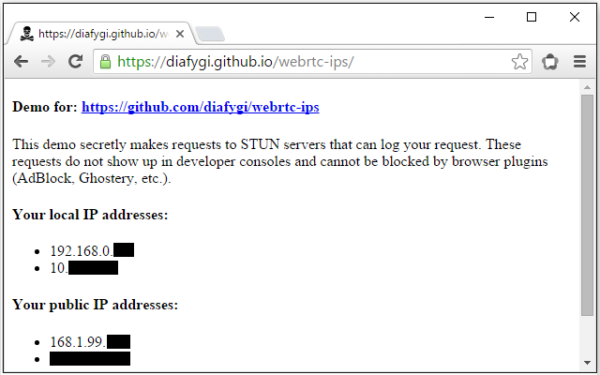
WebRTC
This is where things get complicated.
WebRTC is a new communication protocol that relies on JavaScript that can leak your actual IP address even when connected to your VPN in some cases.
We would not call it a leak, it is just the way this protocol works. This is where you have to decide how much you want to expose your system to the Internet. It comes down to how much you want to educate yourself and put additional efforts to protect your privacy.
More information regarding this can found as the following link:
https://github.com/diafygi/webrtc-ips
There are a number of things you could do like use an free/libre web browser like Mozilla Firefox with plugins like “NoScript” or as an alternate solution block the protocol directly by accessing the browser configurations. Once you are done with it, you have now secured your web browser from potential WebRTC leaks.
VPN Firewalls
Don’t we all lock the door when we are leaving our house or when we are asleep or in general to prevent dirt or unknown persons from entering our home? I guess we all do. An online computer is just like that. Hence a ‘firewall’ (Any of a number of security schemes that prevent unauthorized users from gaining access to a computer network or that monitor transfers of information to and from the network) is a must. Every modern OS comes with a built-in firewall. It is recommended to keep your firewall enabled all the time since Day 1 or your first boot.
We recommend you to check your OS’s firewall and enable it immediately if it is not for some reason. Just because your OS comes with a firewall it is not necessary that it is enabled by default.
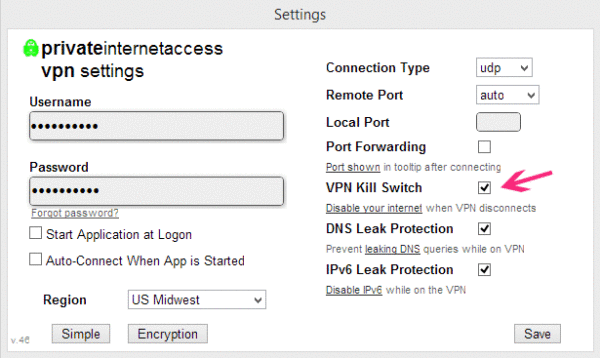
What is VPN firewall or a kill switch?
VPN firewall or a ‘kill switch’ can be defined as a set of firewall rules designed to prevent unencrypted Internet access or to specifically allow Internet access via a VPN tunnel/server. Thereby preventing any sort of leaks that might occur owing to abrupt disconnection of VPN while you are not actively monitoring your system or using it.
A VPN firewall or kill switch could be implemented in a number of ways depending on how you want to do it or your preferences. We would recommend doing it manually so that you are aware of what you are doing.
Traditionally, a custom software for a VPN service is developed and it manages the ‘Kill Switch’ function for you. There are some issues involved. For example the software could crash and then your firewall rules might not be working since it was designed in such a way that rules are only active until the software is open etc. Or it could be leaving some of the firewall rules behind even when it is completely closed which might cause issues later on. Also most custom VPN softwares are not not well maintained and not using production ready stable OpenVPN releases, you could be using a vulnerable or defective OpenVPN version which is the very core of VPN tunneling.
If your privacy VPN provider does not offer you a custom application for your platform with built-in killswitch or VPN firewall, we would recommend you to look into tools like iptables for Linux, pf for BSD or Mac, built-in killswitch protection on recent version of Android OS.
While settings up your killswitch or VPN firewall manually, the idea is to block or drop every connection but connection to the VPN server at a particular port using a specific protocol. And allowing all connections exclusively via VPN tunnel. Such that in case VPN connection breaks or disconnects for any reason. That system in a state where the only thing that would work is connection to the a specific VPN server at a particular port using a specific protocol that you configure.
This not being a comprehensive guide we have to sum up with basics only. But I would like to mention a protocol that your privacy VPN provider should use or implement called WireGuard. Why? It does try to address and actually fix all the major issues. It has built-in killswitch they way it setup on a VPN client, once you turn it on, it won’t let any data go through unless it is via the tunnel. It also makes it very easy for the privacy VPN providers to give IPv6 protection to all their clients or users.
WireGuard is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. It aims to be faster, simpler, leaner, and more useful than other VPN protocols including but not limited to OpenVPN and IPSec. As you probably know, WireGuard is in stable beta and being heavily developed as we speak, but even in its unoptimized state it is up to four times fast than popular OpenVPN protocol and delivers much lower ping time in comparison.
WireGuard aims to be as simple to configure as SSH. A connection is established by an exchange of public keys between server and client just like SSH keys and only a client with its public key present in server configuration file would be authorized.
It would be truly appreciative if your privacy VPN provider happens to be aware of it and is already offering you Wireguard even before it is mainstream, it reflects promptness and zeal to provide better technology at hand to its users. Do consider company’s adoption capability other than customer care, number of VPN server locations and of course privacy policy that it offers.
That is all for now. Stay safe, be alert!














2 Responses to Understanding privacy VPN in nutshell