3 Revolutionary Developments That Are Making Encryption More Accessible
Encryption has long been one of the most important tools in the fight against unwanted surveillance, cyber crime, and corporate espionage, so it is perhaps surprising that, despite the fact that high profile data breaches and international spying scandals are making headlines every month, encryption has not become a more popular tool.
Encryption software, when properly installed and used, provides the gold standard in communication protections. Impossible to crack or circumvent, encryption guarantees the end-to-end security of any message sent — so why isn’t it more widely used?
One of the most likely reasons is simply that encryption can be cumbersome. Encryption requires messages to be disguised using a special algorithm that is locked or unlocked using an electronic key, and the trade-off with traditional encryption technology has generally been that better security comes at the cost of ease-of-use. With the newest encryption technology, however, this has changed. Responding to the needs of their user bases, encryption providers have made a number of stunning breakthroughs in the past year that improve functionality while also beefing up security. Here are three of the most significant:
1. Instant Messaging
The most popular form of electronic encryption has, for more than two decades, been PGP (“Pretty Good Privacy”), an open-standard software that provides high levels of security. But PGP is also limited to email, which means that many of the most popular communication tools, such as instant messaging, are unavailable — or were unavailable, until a new encryption company called ChatMail Secure designed their new proprietary ChatMail Advanced Messaging and Parsing Protocol (CAMP) to give users the functionality of instant messaging while preserving the security of encryption email earlier this year.
2. Integrated Interfaces
Interface design is an important design consideration for any electronic device, but it is especially important in the case of encrypted smartphones. Because users often need to juggle several different levels of encryption in their conversations with people inside and outside their organizations, creating an interface that is simple and effective is vital.
Serious breakthroughs have been made in interface design in the past year that allow users to simply and intuitively send and receive encrypted messages, and to toggle between contacts using different encryption protocols with ease. These developments expected to have a long-term impact on the number of people who choose to adopt encryption software to protect their communications.
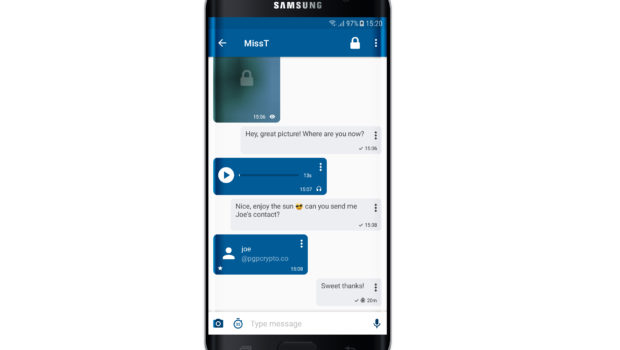
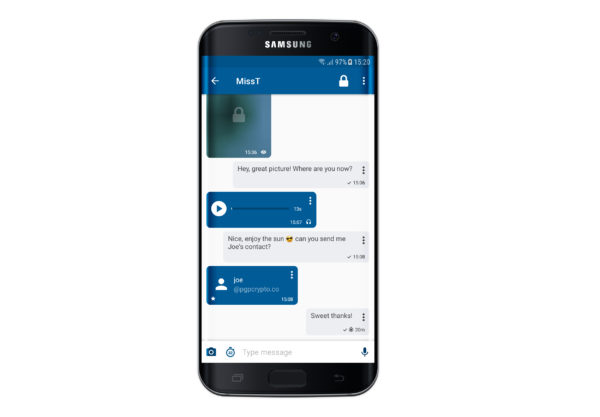
3. Image and Voice Messaging
Encryption users have long complained thatencryption software makes it difficult to conduct business in a comfortable or intuitive way because it strips away tools that allow them to send and receive voice messages and images. The innovative array of tools people can regularly access using unencrypted smartphones has raised the bar in terms of what people expect from their communication tools, which in turn has amplified the calls for a greater range of functionality in encrypted phones.
One of the most consistent requests has been for encryption options that allow users to exchange image and voice messages, which is why it is so significant that these capabilities are finally here. An encrypted smartphone that can send instant messages, pictures, and voice messages rivals the functionality of the most basic smartphones, making it an increasingly attractive option for consumers who don’t want to trade functionality for security.
As awareness about cyber surveillance grows, more and more businesses are looking for ways to protect their communications. Encryption provides the best possible standards of protection, and as it becomes easier to use, more intuitive, and more accessible, it is likely that the number of people and organizations who turn to encryption as a communications solution will grow as well.