Safeguarding IT and digital resources is one of the biggest concerns nowadays. Organizations hire third parties to audit their entire infrastructure so that they may find possible loopholes. These unimaginable glitches can lead to severe and destructive vulnerabilities and turn into cyber attacks. 2021 has been a remarkable and record-breaking year in reporting data breaches. Preceding through 2022 with the same infrastructure and protocol layers would not be a sane idea.
With each minute $29, 00,000 is lost in the name of cybercrimes. Why? According to senior IT specialists and management, it is believed that their digital setup is not robustly secured to resist foreign attacks. For this they need IT audits, testing, and assessment to deeply point out any left behind exposures and susceptibilities in their systems. One of the most widely used and practiced assessment and audit criteria is VAPT (vulnerability assessment and penetration testing).

Image by Freepik
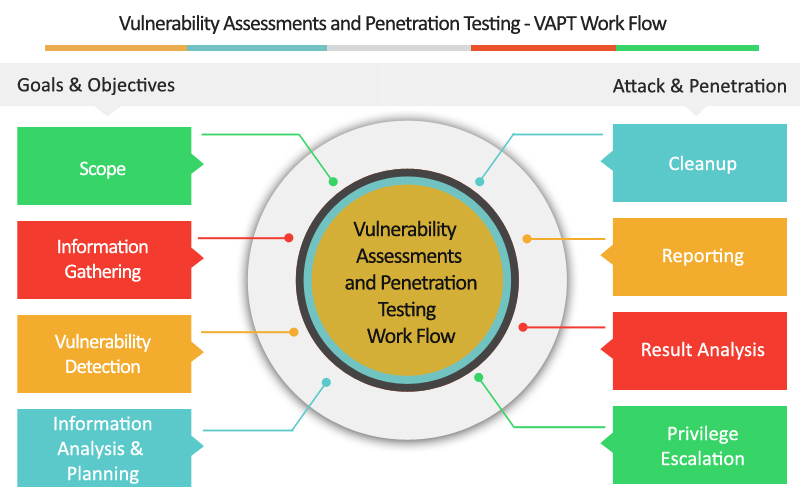
What is VAPT?
VAPT stands for vulnerability assessment and penetration testing and is readily used for auditing security of IT setups. Under the process of vulnerability assessment and pen testing, computerized and high-level programming tools are used to analyze the security status of an organization’s IT environment.
If we split these two terms then vulnerability testing is to assess the ambiguities in the information systems of information technology. This evaluation is meant to be an in-depth estimation of migration processes weaknesses, their entire audit, and also mitigate them to an appropriate level of risk. To pinpoint the data flow lacking in internal and external levels of these IT infrastructure vulnerability testing is needed.
On the other hand, pen testing or penetration testing is to assess the penetration level of attackers and the posed harms by them to the organization’s sensitive information. All the viable security susceptibilities are identified under pen-testing. These exposures are identified, exposed, determined, and then safeguarded by extremely experienced IT and cybercrime specialists. In simplest words, penetration assessment is meant to analyze the range of exposure and destructive capacity of any cyber attacker.
What does VAPT do actually?
- VAPT can be used to test the specific project, product, web application or any mobile application developed.
- Application pen testing can be used to identify and test the defenselessness of a newly launched application.
- To assess the exposure of any network and possible data breaches through these network loopholes through advanced testing services.
- External infrastructure can be assessed with pen testing and assessment to see if it is posing any harm to the internal system.
- Likewise, the internal system is assessed, audited, and analyzed to find out any security concerns and needed amendments.
- For third parties, VAPT providers work as IT auditors, but they do not only identify the exposures and weaknesses but also cater them to sufficient levels of protection measures.
- Instead of being single standalone testing, these practices (VAPT) are hybrid in nature. It does involve comprehensive evaluation and assessment of IT-related procedures.
- Source codes of mobile applications and web-based applications are reviewed to ensure the maximum security and safeguarding of these applications and systems.
- Functionality testing is another perk of VAPT, to test any newly developed product whether it is functionally ready to be launched in the market.
- To audit and assess the non-functional requirements of web and mobile applications, security solutions and systems VAPT is the most reliable and authentic way.
Perks of having a VAPT service provider
Reduced cost of re-evaluation
We do not deny the fact that in the first place you have to spend a handsome amount for the complete assessment and evaluation of your entire organization’s IT setup, either internal or external. But this cost is sufficiently reduced. Test cases and evaluation criteria are set, no overhead, additional and hidden costs would be borne by the organization in re-evaluation.
Better and improved IT security practices
Once you have tasted the VAPT for your organization, you will never set for less. VAPT makes sure to not just identify but evaluate the ranges and penetration of possible cyber-attack. This makes the entire organization conscious and determined to practice better IT security measures at every end. In other words, VAPT makes you perform better and improve IT security practices.
A systematic and practical way to align with security compliance requirements
For IT and digital service providers, it is necessary to have security compliance and before that they need to make sure their infrastructure is robust enough. For this purpose companies first opt for VAPT to recognize the breaches, insecurities,, and weaknesses in their systems.
Complete and comprehensive assessment based on the worldwide used criteria
VAPT services are provided by third parties as security audits. Worldwide recognized and used criteria and tests are implemented to evaluate systems and applications at each end.


