WAF Security: What It Can Do to Your Business
There has been a seeming mad scramble of enterprises to leverage a constant online presence. After the initial success generated by putting up their websites, everyone is upping the ante. This time, everyone is moving to cloud-based services and web applications. While everyone’s firewalls grew with the trend, a typical website owner is still unaware of WAF security.
The situation is quite understandable, especially since most organizations have long been satisfied by security measures at the user level. That is, they generally protect their end with security software and a firewall. That pretty much worked until the use of cloud computing and web applications exploded.
While these developments did improve a customer’s experience and engagement with a business’s online presence, it opened unprecedented levels of risk. Traditional firewalls are no longer enough to contain malicious attacks. The fact is over 70% of all reported data breaches account for web application attacks.
Enter the WAF
The question now is what a website owner must do to counter these increasing and highly-complex attacks. The good news is that it does not require you to have a dedicated IT team, much less overhaul one. What you need is to deploy a web application firewall solution, or WAF security, as part of your existing DNS service.
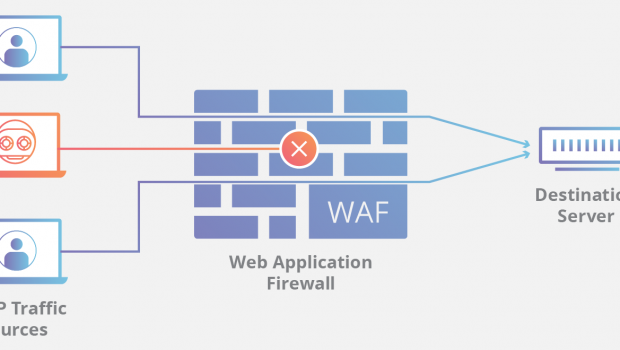
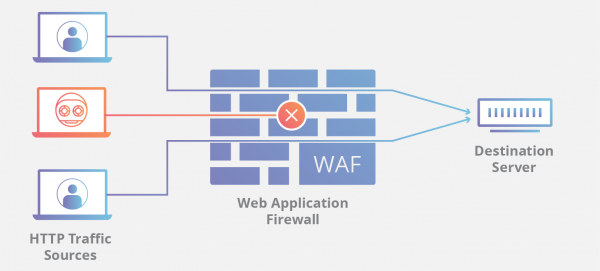
To better understand how it works, imagine WAF as a sort of intermediary service. Your website could have several web applications like online forms, shopping carts, and email programs. The WAF stands between these applications and your website’s users. What it does is monitor and stop any malicious request from getting in and causing damage.
You must take note, though, that WAF does not replace traditional firewalls. You would still need the perimeter-like protection offered by a standard firewall to your network. The operation of a WAF is specific only to running security on web applications. Thus, the security should complement existing security protocols, not replace them.
Selecting a WAF
There are three deployment options for WAF security. Without digging too much in each option’s technicality, it suffices to say that the first two, in-line appliance and end-point, have specific installation and configuration requirements. It follows that you will need or have to hire technical expertise to implement any of these two WAF architectures.
The deployment of the in-line appliance architecture is within your organization’s network and is platform agnostic. That means it can run on any existing operating systems such as Linux, Mac, Unix, or Windows. Meanwhile, the end-point WAF gets deployed within the host server and is platform-specific. However, this option requires constant oversight with the website owner.
On the other hand, you can place the tinkering of the WAF’s configuration, tuning, and maintenance in the hands of your service provider. You can do that by opting for cloud-based WAF deployment.
Just like the first deployment option, cloud-based WAF architecture can run on your existing operating system. Since the protection is cloud-based, the WAF is outside your hosting environment and configured by the DNS service provider for you. By doing so, you free yourself from the technical oversight and receive automated patches and updates every time.
Having all three WAF deployments is the highest level of protection you can apply. Still, you will need to consider which option suits best your organization. In terms of practicability and convenience, you can achieve an all-around performance by getting cloud-based WAF security for your organization. What is critical, ultimately, is to have one as an integral part of your website.