5 most overlooked security threats
Most businesses are aware of the biggest security threats out there, but it is important to also watch out for lesser-known dangers to avoid any nasty surprises. Security breaches don’t always stem from the most obvious of places and businesses must be prepared for all threats, small and large.
In this article, the experts at Syntax IT Support London highlight five of the most overlooked security threats that you should be made aware of.
Internet of Things
Smart IoT devices are increasingly used in our everyday lives, but many of us don’t even consider them when it comes to keeping networks secure. Businesses can be put at risk by smart devices in employees’ homes as more people than ever work from home. Once outside of the office’s secure network, business data is vulnerable and smart home devices provide more entry points for hackers. Laptops containing sensitive data are connected via the Internet of Things to the same network as, say, an employee’s smart fridge. If the fridge is hacked, corporate data is also under threat. Businesses need to take the threat posed by the Internet of Things more seriously and consider how they can mitigate these risks.
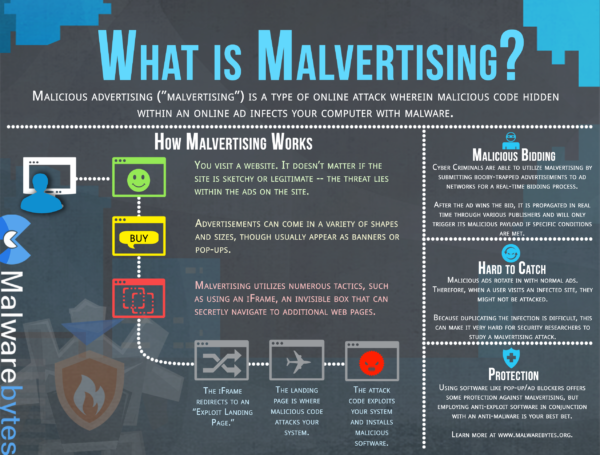
Malvertising
Malvertising has re-emerged recently as attackers have begun to target the websites of smaller brands and businesses. It is assumed that these businesses will focus less on the content of ads on their pages, as they don’t place as much importance on visitor numbers. Malicious ads allow attackers to generate revenue but they can also be much more sinister than this. Malvertising can be used to collect identities or install malware onto a machine, which is a serious security issue for anyone who has clicked on the wrong advertisement. To protect themselves and site visitors, businesses should use full-time employees to manage websites, or ensure that contractors are checking source code to monitor for malicious ads. Patching systems and using ad blockers can also mitigate the risk of malvertising.
In-memory attacks
In-memory attacks are more common than most people are aware, but they are difficult to monitor for even by antivirus software. Malware is executed when an infected Word or Excel document is launched, or when the victim visits a malicious webpage. There is no sign of the attack once a system is rebooted, so it is incredibly difficult to catch the culprit. Devices are vulnerable to in-memory attacks when unneeded macros are enabled on them. Businesses can protect themselves by disabling any unnecessary macros.
Mobile devices
Employees are using mobile devices such as phones and tablets more than ever, and not just for personal use. As technology has improved we’ve started to use our mobile devices for work, which means company data has also become mobile. These devices are more vulnerable than laptops and desktop computers and it is important that they be secured properly. Data must be stored in the correct place and not in personal cloud accounts, as this puts sensitive information at risk and is also in breach of data protection laws. Businesses should include steps to keep mobile devices secure in their IT policies and clearly instruct employees on how to protect business data as well as their own personal information.
Lack of employee awareness
Businesses only chance to protect company data is if each of their employees works to protect it also. Many employees do not have an in depth understanding of data security, simply because businesses do not focus enough on thoroughly training them in this area. Security and privacy training should be extended to every employee, as hackers are known to target lower-level employees who still have access to sensitive data. All businesses must realise the importance of thorough data security training, as we are all constantly online and are putting our information at risk.
Businesses are aware of the importance of security and put a lot of resources into protecting themselves against attacks, but it is vital that lesser-known threats are considered and are protected against just as thoroughly as those which are more prevalent.