The Biggest Threats to Your Computer Devices
When it comes to protecting your devices, the best strategy is one of vigilance. Being aware of what could bring your devices to harm, and knowing how to prevent it, will make you far less likely to lose data and time to malware. Cybercriminals are constantly playing a game of cat and mouse with software companies. They are always trying to find loopholes to exploit and ways of duping customers into partying with their valuable information.
Ransomware
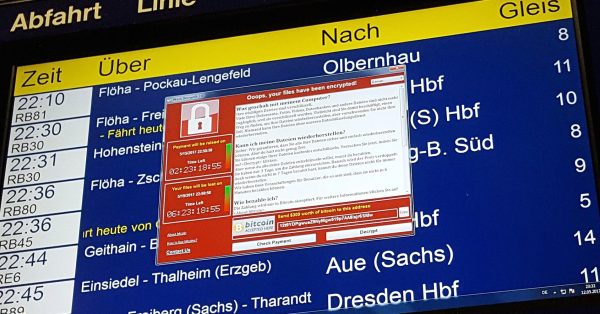
Even the word ‘ransomware’ strikes fear into many people. This type of malware works much like many other forms of virus; it gets into your system by encrypting your files. However, there’s a much more malicious streak to this type of crime — the criminal will ask for a payment in order to gain access again to the files. This will usually be done in a particularly currency or a cryptocurrency like Bitcoin. The only way to get rid of ransomware is to either pay the ransom (never advised) or use ransomware removal.
Lack of Knowledge
Educating yourself about the risks to your device is one of the best ways to protect yourself and your information. Cybercriminals benefit hugely from victims’ lack of knowledge, and by leaving yourself vulnerable to this, you are playing right into their hands. Reading up on what modern phishing scandals look like, how to protect your web browsers, and how to protect devices at the most basic level, is the best place to start.
Computer Virus
A bog standard computer virus is still the biggest threat to most personal devices. This is because the way they’re installed onto your computer is so simple and so easy to accidentally initiate. They’re often downloaded on files such as attachments on emails or from unreliable websites. It’s worth knowing that these can then plague you with spam, or temporarily interrupt your security settings. Deleting information on your hard-drive and maybe even stealing your private information are some of the real consequences of these pieces of malware. The best way to prevent them is to be cautious about the websites you use, the documents you download and to install security software.
A Trojan
If you think a trojan is just another type of computer virus, then think again. Trojans are, strictly speaking, not computer viruses, but are rather different forms of malware. A trojan works by pretending to be something completely different before weaving its way onto a device. It appears ostensibly harmless, but within it is something very harmful for your computer. A traditional computer virus will emend itself into the code of a program on your device and will use the software to reproduce. Trojans can easily be removed with anti-malware or by a computer technician, but the best way to stop this from happening is to avoid downloading suspicious files.
Phishing Scams
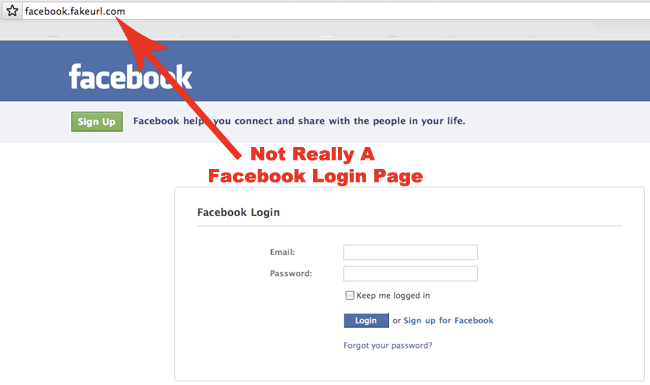
Phishing scams may seem comparatively retro these days, and yet they are still incredibly useful for harvesting personal information. These are used on both personal and business users alike, which means that anyone is a potential victim. They are incredibly effective at getting a hold of valuable usernames and even the passwords to particular documents. Senior citizens are particularly vulnerable to these attacks as most of them lack the know-how to detect these attempts. Which is why it is crucial for computers to have a form of internet security for elders so that these attempts can be negated.
Phishing scams are perhaps so effective because of the convincing front the hackers put up to victims. They masquerade as trustworthy figures or even as institutions such as banks. The second you hit ‘reply’ is the moment they instantly have information about you.
If you have received an email that you suspect might be a phishing scam, then here are a few signs to look out for:
- It’s trying to replicate an email from a subscription service you already use, such as a television and movie service. You will notice that a few details might be slightly off or incorrect.
- A generic greeting: most reliable and professional companies have the tools to address you personally, even on a chain email.
- It accuses you of missing a payment — before you do anything at all, go and double-check whether this is indeed true.
- A suspiciously irrelevant need for you to fill in your contact and payment details.
If you have been the victim of a cyberattack, there’s no reason to feel any shame about this: modern cybercriminals are incredibly adept at praying on our most basic instincts online. They use trusted websites and personalities to get a hold of our personal information. They best way to prevent against this is to download effective anti-malware software to intercept these criminals first.